100+免費的業界威脅情報感知資訊

威脅情報感知 — 什麼情況下會需要用到呢?
- 有異常的內部電腦連線到特定 IP, 我想知道該 IP 是否是已知的殭屍網路?
- 有異常的檔案 Hash, MD5, SHA1 想進一步查詢該 Hash 是否是病毒?
- 網站 Domain, URL 等訪問, 該Web, URL 是否有害?
- 業界是否有已知的 IP 黑名單可以加入更新到防火牆?
業界已有許多這些威脅情報可以供我們使用, 讓我們進一步查詢與進行威脅分析
這篇文章主要介紹幾種常見的免費威脅情報感知的資訊
參考 https://www.threatq.com/integrations/
VirusTotal
這是最常用也是最知名的線上威脅分析, 可以分析可疑檔案
上傳之後雲端會用超過60種防毒軟體進行掃描, 並且回報掃描的結果
不需要註冊任何帳號就可以使用, 註冊帳號之後可以用 API 查詢
另外也提供桌機版本可以使用 https://www.virustotal.com/en/documentation/desktop-applications/

Malwr
這是一個線上沙箱的服務, 提供可以檔案的靜態分析, 與執行時的動態分析
動態分析包含該檔案執行過程中會遺留的檔案, 行為, 存取的註冊碼, 往外連線IP, domain 等

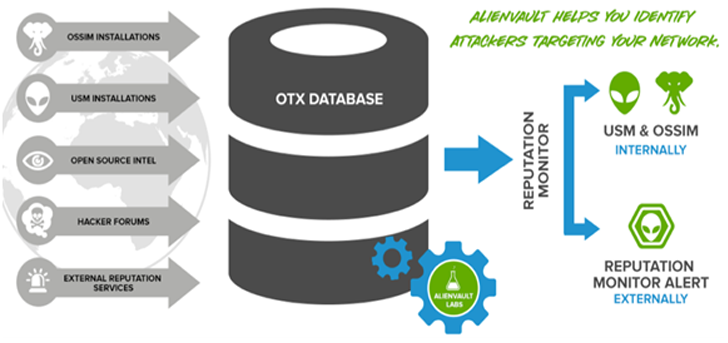
AlienVault Open Threat Exchange
https://www.alienvault.com/open-threat-exchange
AlienValut 除了提供類似Virus Total 的服務外, 更像是一個論壇
上面有許多安全專家會相互分享發現的APT攻擊軌跡IOC (Indicator of Compromise) or YARA等
需要註冊一個免費的帳號之後就可以使用
CyMon Open Threat Intelligence
一個類似 VirusTotal 的服務, 額外的是搜尋結果會把歷史最近相關的安全事件列出
除了雲端版本之外, 還有桌機版本可以下載使用 http://download.cymon.io/

ThreatMiner
https://www.threatminer.org/index.php
這服務的特色是提供 PDF , CSV等可以將分析報告結果下載,
另外也提供相關的 APT 分析報告

Malware Information Sharing Platform (MISP)
上述介紹的都是雲端服務, 如果企業內部想要自行搭建類似的服務呢?
可以使用這個開源的平台, MISP, 提供 VM Image 下載後就可以搭建一個威脅感知分析的資訊平台
![]()
Hybrid-Analysis
https://www.hybrid-analysis.com/
CVE & CWE
由於病毒與威脅都是透過漏洞, 這個服務提供漏洞查詢簡便的方式
https://cve.circl.lu/cve/CVE-2017-13753


RiskIQ (PassiveTotal)
https://community.riskiq.com/search

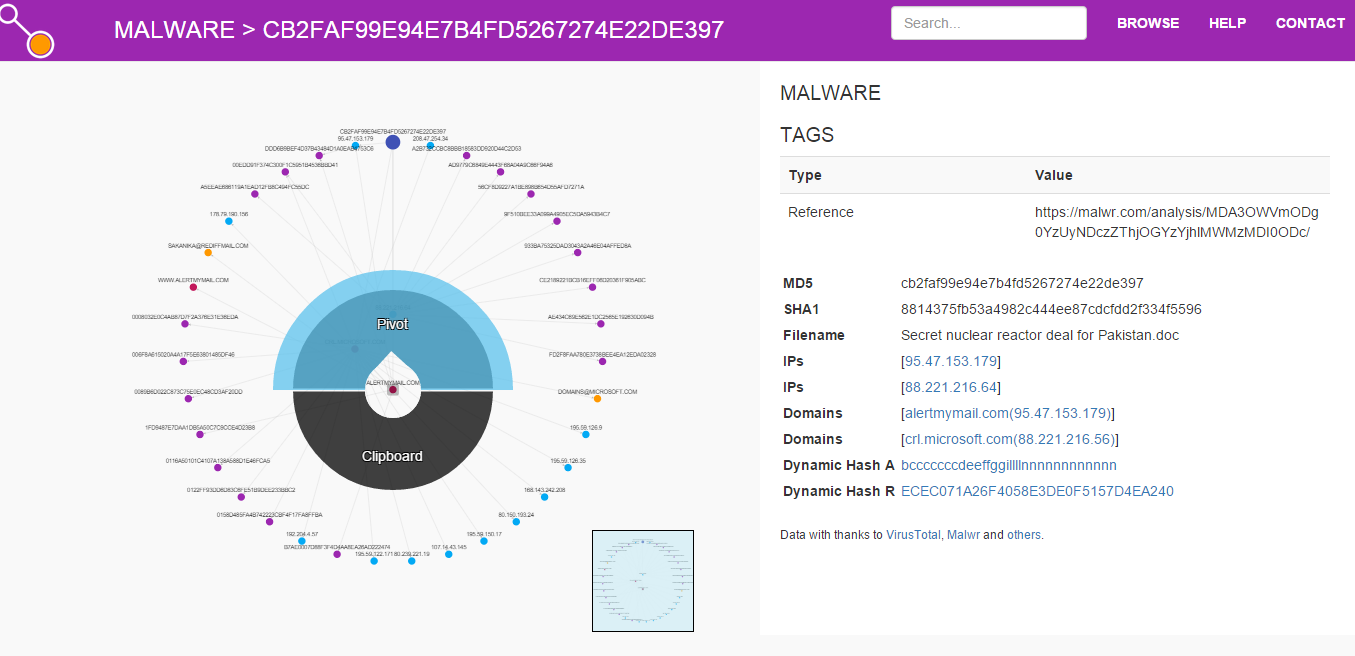
ThreatCrowd
這是一個免費開源的線上威脅分析
特別的是該服務呈現方式是用關聯圖的方式將相關的資訊整體呈現
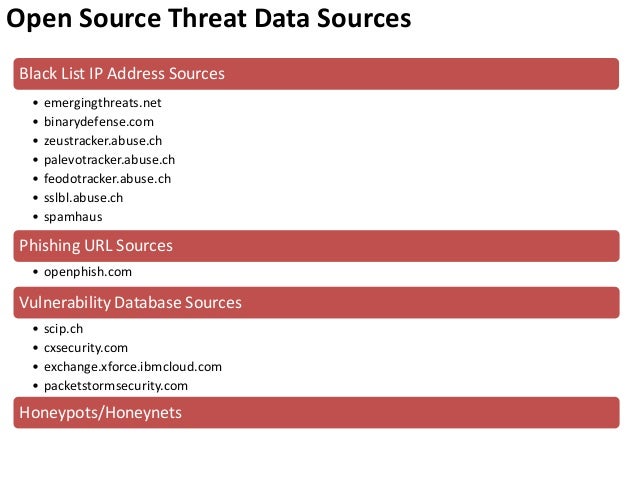
IP 黑名單
接著介紹幾個知名的 IP黑名單資訊
病毒Hash資料庫
http://www.malshare.com/daily/
- http://www.malwaredomainlist.com/mdl.php
- http://www.malwareblacklist.com/showMDL.php
- http://support.clean-mx.de/clean-mx/viruses.php
- http://malshare.com/ (registration required)
- http://malc0de.com/database/
- https://zeustracker.abuse.ch/monitor.php?browse=binaries
- http://www.sacour.cn/showmal.asp?month=8year=2012
- http://malwaredb.malekal.com/ (registration required)
- http://blog.urlvoid.com/new-list-of-dangerous-websites-to-avoid
- http://www.scumware.org
- http://www.threatlog.com
- http://adminus.net (For sample requests use contact email adminus.xs(at)gmail(dot)com)
- http://jsunpack.jeek.org/?list=1 (RSS feed)
- http://www.malwareurl.com/ (free registration required)
- http://www.offensivecomputing.net/ (malware repository, free registration required to download)
- http://vxvault.siri-urz.net/ViriList.php (password required, unknown at present)
- http://vxvault.siri-urz.net/URL_List.php
- http://contagiodump.blogspot.com/2011/03/take-sample-leave-sample-mobile-malware.html (Mobile malware samples)
- http://virussign.com/downloads.html (registration required)
- http://www.nothink.org/viruswatch.php
- http://dashke.blogspot.com/
- http://malware.lu/ (registration required to download)
- http://www.nictasoft.com/ace/malware-urls/
- http://virusshare.com/
- http://labs.sucuri.net/
- http://freelist.virussign.com/freelist/
- http://malwareurls.joxeankoret.com/normal.txt
- http://malwared.malwaremustdie.org/index.php?page=1
- http://ytisf.github.io/theZoo/
- http://amtrckr.info/
- http://malwaria.cf
- Contagio Malware Dump: Free; password required
- Das Malwerk: Free
- FreeTrojanBotnet: Free; registration required
- KernelMode.info: Free; registration required
- MalShare: Free; registration required
- Malware.lu’s AVCaesar: Free; registration required
- MalwareBlacklist: Free; registration required
- Malware DB: Free
- Malwr: Free; registration required
- Open Malware: Free
- theZoo aka Malware DB: Free
- Virusign: Free
- VirusShare: Free
Emergingthreats
https://rules.emergingthreats.net/blockrules/
Feodo Tracker
https://feodotracker.abuse.ch/
![]()
ZeuS blocklist
https://zeustracker.abuse.ch/blocklist.php
MalwareDomainlist
- https://www.malwaredomainlist.com/mdl.php
- https://www.metadefender.com/threat-intelligence-feeds
- https://openphish.com/feed.txt
- https://isc.sans.edu/suspicious_domains.html
- Malware Domain List.com
- Domain Blocklist From Malwaredomains
- Abuse.ch Ransomware Domain Blocklist
- Threatexpert.com Malicious URLs
- Zeus Command And Control Server from Abuse.ch
AWS WAF 用的 IP Reputation list
- https://www.spamhaus.org/drop/
- https://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt
- https://check.torproject.org/exit-addresses
當發現有異常Domain的訪問時?
可以利用網上一些業界開源工具得知該Domain是否為已知有害威脅
舉例來說, “eovighu.com” 是否為已知威脅來源? 可用下列方式搜尋
| IBM X-Force Exchange IP Lookup | |
| AlienVault IP Lookup | |
| Cymon.io IP Lookup | |
| ThreatMiner IP Lookup | |
| MISP SHA2 Lookup | |
| MISP MD5 Lookup | |
| VirusTotal SHA2 Lookup | |
| VT Private SHA2 Lookup | |
| AlienVault SHA2 Lookup | |
| ThreatMiner SHA2 Lookup | |
| ThreatMiner SHA2 Metadata | |
| VirusTotal MD5 Lookup | |
| VT Private MD5 Lookup | |
| AlienVault MD5 Lookup | |
| ThreatMiner MD5 Lookup | |
| ThreatMiner MD5 Metadata | |
| CIRCL CVE Lookup | |
| IBM X-Force Exchange EFQDN Lookup | |
| VirusTotal EFQDN Lookup | |
| PassiveTotal EFQDN Whois | |
| PassiveTotal EFQDN OSINT | |
| PassiveTotal EFQDN Malware | |
| ThreatMiner EFQDN Whois | |
| ThreatMiner EFQDN Hashes | |
| VirusTotal SHA1 Lookup | |
| VT Private SHA1 Lookup | |
| AlienVault SHA1 Lookup | |
| ThreatMiner SHA1 Lookup | |
| ThreatMiner SHA1 Metadata | |
| Censys.io IP Lookup | |
| Shodan IP Lookup | |
| ThreatCrowd IPv4 Lookup | |
| ThreatCrowd MD5 Lookup | |
| ThreatCrowd FQDN Lookup | |
| BlockChain Address Lookup |
- Artists Against 419: Free; lists fraudulent websites
- ATLAS from Arbor Networks: Free; registration required by contacting Arbor
- Blackweb Project: Free; optimized for Squid
- CLEAN-MX Realtime Database: Free; XML output available
- CriticalStack Intel Marketplace: Free; registration required; optimized for Bro
- Certly Guard: Free tier available; registration required; query database via API
- CYMRU Bogon List: Free
- DShield Blocklist: Free
- FireHOL IP Lists: Free; combines several blacklists from other sources
- Google Safe Browsing API: Free; programmatic access; restrictions apply
- hpHosts File: Free; limited automation on request
- Malc0de Database: Free
- Malware Domain Blocklist: Free for non-commercial use
- MalwareDomainList.com Hosts List: Free
- Malware Patrol’s Malware Block Lists: Free for non-commercial use
- MalwareURL List: Commercial service; free licensing options may be available
- OpenPhish: Phishing sites; free for non-commercial use
- PhishTank Phish Archive: Free; query database via API
- Project Honey Pot’s Directory of Malicious IPs: Free; registration required to view more than 25 IPs
- Scumware.org: Free
- Shadowserver IP and URL Reports: Free; registration and approval required
- Squidblacklist.org: Paid and free options available
- VoIP Blacklist: Free; specific to VoIP abusers
- ZeuS Tracker Blocklist and URLs: Free
- www.BlockList.de: Free
其他相關威脅情報
abuse.ch Ransomeware Tracker Source
abuse.ch ZeuS Tracker Source
AVG Website Safety Reports
http://www.avgthreatlabs.com/en-ww/website-safety-reports/
Bambenek Source
https://osint.bambenekconsulting.com/feeds/c2-ipmasterlist.txt
https://github.com/firehol/blocklist-ipsets
Blocklist.de source
http://www.blocklist.de/en/index.html
BotScout Bot list Source
http://botscout.com/search.htm
Botvrij
http://www.botvrij.eu/data/
http://botvrij.eu/
#Emerging Threats Community
emerging_threat_compromisedIP = “http://rules.emergingthreats.net/blockrules/compromised-ips.txt”emerging_threat_blockedIP = “http://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt”emerging_threat_russian_IP = “http://doc.emergingthreats.net/pub/Main/RussianBusinessNetwork/RussianBusinessNetworkIPs.txt”emerging_threat_malvertisers = “http://doc.emergingthreats.net/pub/Main/RussianBusinessNetwork/emerging-rbn-malvertisers.txt”
#OpenBL ProjectopenBL = “http://www.openbl.org/lists/base.txt”
#Project Honeynethoneypot_ip = “http://www.projecthoneypot.org/list_of_ips.php?rss=1”
#SANS Institutesans_ip = “https://isc.sans.edu/ipsascii.html?limit=2000”
#Blocklist.deblock_list = “http://www.blocklist.de/lists/all.txt”
#AlienVault IP Reputationalien = “https://reputation.alienvault.com/reputation.generic”
#Abuse.ch zeus trackerzeus_tracker = “https://zeustracker.abuse.ch/blocklist.php?download=ipblocklist”
#Team-Cymru Dragon Research Groupvncprobe_ip = “https://www.dragonresearchgroup.org/insight/vncprobe.txt”ssh_ip = “https://www.dragonresearchgroup.org/insight/sshpwauth.txt”
#Malc0de Blacklist IPsmalcode_ip = “http://malc0de.com/bl/IP_Blacklist.txt”
#Malware Domain List (MDL) Malware C&C IPsmdl_ip = “http://www.malwaredomainlist.com/hostslist/ip.txt”
#TALOS IP Blacklisttalos_ip = “http://talosintel.com/files/additional_resources/ips_blacklist/ip-filter.blf”
#CI Army Bad IPsci_army_ip = “http://www.ciarmy.com/list/ci-badguys.txt”
#NoThink.org Honeypot Project By Matteo Cantoninothink_dns = “http://www.nothink.org/blacklist/blacklist_malware_dns.txt”nothink_http = “http://www.nothink.org/blacklist/blacklist_malware_http.txt”nothink_irc = “http://www.nothink.org/blacklist/blacklist_malware_irc.txt”nothink_ssh = “http://www.nothink.org/blacklist/blacklist_ssh_all.txt”
#TOR exit nodestor_exit_nodes = “https://check.torproject.org/exit-addresses”
#korean & Chinese Spam IP feed
korean_ip = “http://www.okean.com/korea.txt”
#Bad IPs listr for last 1000 hoursbad_ip = “http://www.badips.com/get/list/apache-wordpress/0?age=1000h”
###List of Domains goes here ###
#Open-phishopen_pish = “https://openphish.com/feed.txt”
#Joewein Blacklistjoewein_domains = ‘http://www.joewein.net/dl/bl/dom-bl.txt’
###Ocasionally updated feeds for Email blacklisting####Joewein Blacklistjoewein_email = ‘http://www.joewein.net/dl/bl/from-bl.txt’
https://pdfexaminer.com/
http://vxvault.net/ViriList.php
http://www.threatexpert.com/
http://blocklist.greensnow.co/greensnow.txt
